Quantum Computers Do Not Pose an Existential Threat to Bitcoin (Part 2)
Quantum computing – an existential threat to Bitcoin?
You can find the first part of this article here.
This content is for informational purposes only, you should not construe any such information or other material as investment, financial, or other advice. Nothing contained in this document constitutes a solicitation, recommendation, or endorsement to buy Bitcoin.
Solutions for attack vectors 1a and b
One option for dealing with the quantum vulnerable Bitcoins discussed in attack vectors 1a and b is to reach a consensus within the Bitcoin community and issue an ultimatum for users to move their funds to a safe address. But the private keys of many owners of ‘quantum susceptible’ Bitcoins have been lost. Therefore, these coins are not transferable and could be claimed by the first person to construct a suitably powerful quantum computer. A proposal may be that coins in unsafe addresses become unusable after a set amount of time (technically, this means that miners will ignore transactions coming from these addresses). Given the difficulty of establishing a consensus on this sensitive issue, such a substantial step must be thoroughly reviewed before being approved.33 On the other hand, if this rule-change is not done in a timely manner, a bounty pool of a few million Bitcoins remains in the open (although every Bitcoin address would have to be cracked individually – adding more time and pressure to change the protocol). A more realistic scenario to occur is that repeatedly conveying the message to the community to not re-use Bitcoin addresses twice and to move their funds to a safe address will decrease the amount of quantum vulnerable Bitcoins significantly. Once a quantum computer appears to attack the first unveiled public keys (or gets closer to achieving this), pressure to finally move funds to a safe address will rise to be the utmost priority for these users. This would result in a substantially decreasing honey-pot of Bitcoins for the quantum computer so that almost only the funds of users that have lost their private keys in the past would be prone to be hacked.
Principles of effective incentive design can be used to speed-up changes in consensus rules, such as applying a markup on transaction fees for P2PK and reused P2PKH wallets. This would prompt users to switch to safer behavior.34
I don’t think it’s likely that there will ever be a consensus established to cut old addresses off the network, given the censorship-resistant properties of the network itself – one of the pillars of Bitcoin. The “code is law” ruling will probably remain dominant.35 The total sum of lost Bitcoins to date is estimated to be around 3,7 million.36 The honey-pot would only be a fraction of that number because most of these “lost Bitcoins” do not have unveiled public keys and therefore cannot be acquired by a quantum computer. All-in-all, it is quite likely that one day, a few hundred thousand Bitcoins will be obtained by a quantum computer.
Whether these implementations to mitigate attack vectors 1a and b fail or not, the “a-few-hundred-thousand-Bitcoins-carrot”, dangling right in front of scientists and engineers worldwide, could act as a stimulus to accelerate the development of this groundbreaking technology.
Solutions for attack vector 1c
The Bitcoin protocol may be modified to meet post-quantum cryptography standards and protect against flaws using the fork mechanism. Unfortunately, this defense mechanism implemented in Bitcoins design is often neglected (or not known) by quantum experts in their predictions of “cracking Bitcoin”.
The history of Bitcoin is filled with examples of hardware and software changes that had to be made to make the network more secure and performant37 — and good security practices in the present (avoiding wallet re-use) can help prepare for a more uncertain future.38 Some of these approaches have been in development for many years.
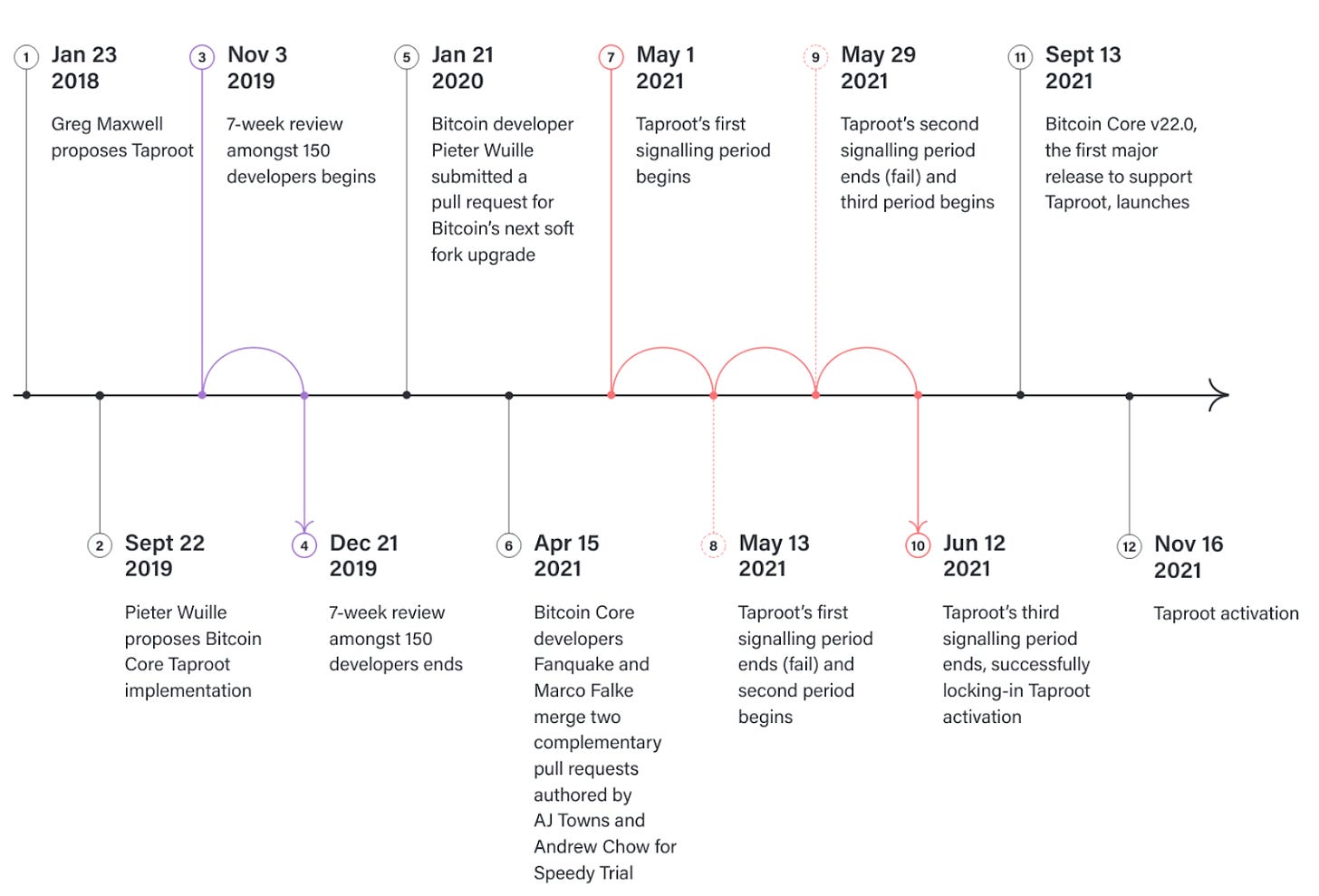
Similar to the recently activated taproot development update, where the timeline of development looked like this:39
Premature optimization of issues that do not exist yet can lead to more significant problems.40
There are many ideas about how to mitigate the risk of effective quantum computing attacks, even with long-term solutions: Lattice-based schemes (GPV, LYU, BLISS, ring-TESLA, DILITHIUM, and NTRU), multivariate polynomials (RAINBOW), and hash-based signatures (LMS, XMSS, SPHINCS, and NSW) are examples of proposals and solutions to the risk of quantum computing.41 However, these typically involve some kind of trade-off, be it higher costs, higher processing power, or greater network traffic.42
Adding to that, various other solutions have existed for many years regarding the serious attack vector described in 1c.43 One of them, suggested by Vitalik Buterin in 2013, is Lamport signatures.44 However, this has some limitations (one-time signatures and management of the same) to remain quantum-safe. NIST post-quantum signature schemes are a better alternative in comparison.45
Other post-quantum cryptography solutions include some zero-knowledge proof schemes.46 The event that quantum computers, which are generally still useless noise-making machines at this point, can derive the private key from the public key within the crucial time window is still some years away. The most optimistic predictions are five years (other, probably more realistic estimates range from 10-20 years), ignoring the fact that the quantum computer would also have to be “trained” to perform this specific task.47
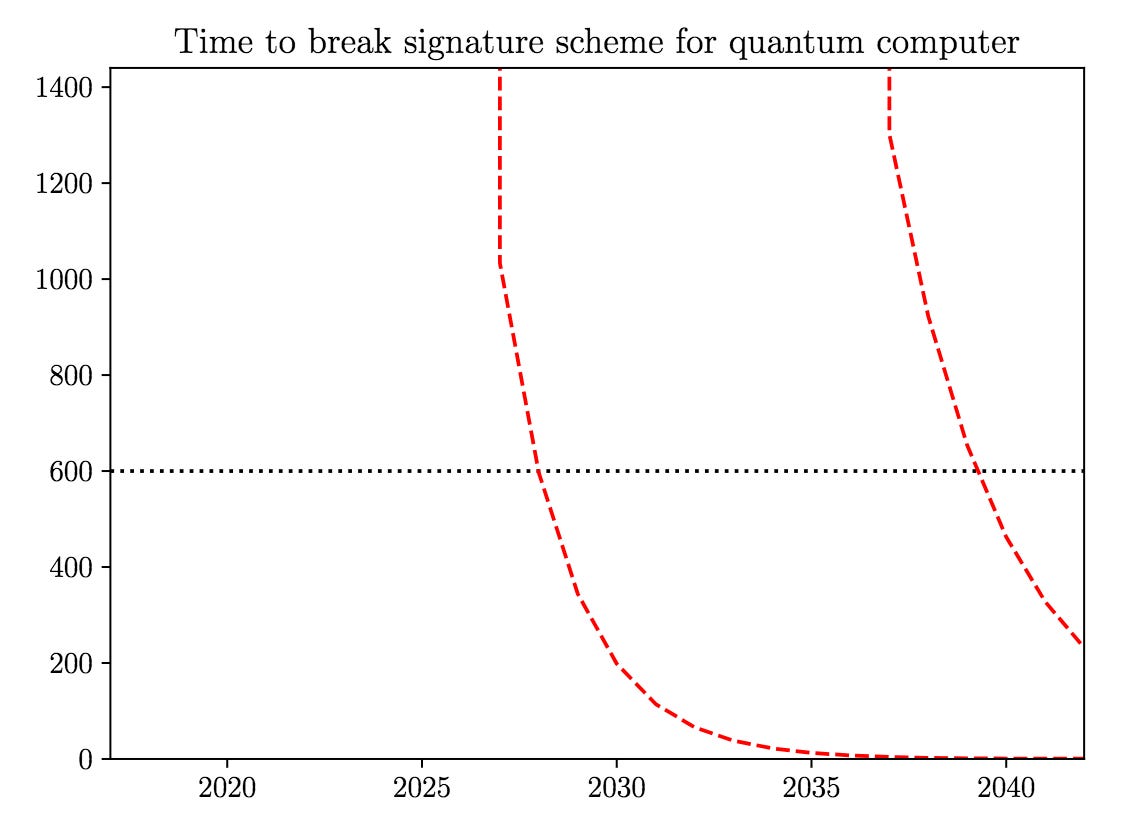
A lot can happen in this timeframe regarding further research to find the most optimal solution. An unconventional and non-protocol-changing idea involves data collection via the mempool APIs to run real-time machine learning algorithms. These could spot anomalies and flag attempts at transaction hijacking.48
Attack vector 2 – Quantum miners
Another area of concern comes on the quantum mining front.
The most likely scenario is that a slow transition to better technology as it becomes available will be the outcome with quantum computing, as is the standard practice today when new hardware is released. Once quantum computers reach a state of development acceptable for mining, a quick adoption among miners can be expected, establishing an equilibrium as the network difficulty adjusts.49
Miners are incentivized to accumulate greater computing power, but they are also rewarded for maintaining the chain’s integrity. It would almost certainly be short-lived if a quantum attack were to happen. Miners would immediately agree and defend the network, demonstrating basic game theory in action. Additionally, the Bitcoin network is safer today than ever before – the hash rate is at an all-time high, with mining facilities located worldwide.50 It’s unlikely that a single person or organization will amass enough processing power to take over the network.51
Additionally, the proof-of-work mechanism used by Bitcoin is relatively resistant to substantial speedup by quantum computers for at least another five years, mainly because ASIC miners are extremely fast compared to the estimated clock speed of near-term quantum computers.52
These five years are an extremely optimistic estimate for quantum computers, as the further exponential advancement of ASICS is not added to the equation. From my research, it seems like the whole quantum mining fear is totally overhyped – the theoretical issues described in attack vectors 1a and b are the most “urgent” to solve, while this one might never become one.
Attack vector 3 – The Quantum Surprise – Sudden, secret, and massive quantum computing advancements
One of the main concerns portrayed in the public realm appears to be someone building an incredibly advanced quantum computer in secret.
This quantum computer would be capable of compromising cryptography throughout the world, but then choose specifically Bitcoin that will almost immediately lose most or all of their value using the most powerful and (probably) expensive machine ever built in human history. That is undoubtedly a danger that should be explored, but it is not realistic, like other “movie plot” risks.53
Attack vector 3a – The Quantum Surprise – Bitcoins cryptography
To minimize this attack from even occurring, a public bounty for anyone who publicly discloses the secret advance of quantum computers while remaining anonymous has been put in place.54 And even if it were to happen, an emergency fork of the Bitcoin network with ready-to-implement solutions exists. These transition protocols even function when ECDSA (used for the generation of signatures in Bitcoin) has already been compromised.55
As an immediate consequence, I would expect an extreme price crash accompanied by newspaper headlines “Bitcoin hacked by quantum computer”. Plenty of digital ink will be spilled. In the middle and long term, on the other hand, the survival of the quantum-proof Bitcoin fork will prove the resilience and adaptability of the network to yet another attack vector. The attacker has revealed their secret weapon that could theoretically break the encryption keys of military intelligence networks, practically throwing away a vast advantage – the ace up their sleeve – for absolutely nothing. It’s fun to discuss this theory in theory, but it’s not going to happen in the real world.
Attack vector 3b – The Quantum Surprise – A 51% attack on the Bitcoin network
For the sake of this article, we are interested in the worst-case scenario – even if it’s improbable to ever happen. We need a combination of:
- a massively unexpected and secretive leap in quantum computing, and
- a quantum computer specialized in mining for Bitcoins that vastly outperforms all ASIC miners on earth, which then
- leads to a possible 51% attack of the network which, of course
- could then be upheld for a more extended time – and not to forget –
- no other competing quantum computer interferes the attack, and
- the actor doesn’t want to support but rather destroy Bitcoin (spending billions and earning nothing).
Now that we have our recipe of unlikely-to-happen and economically pointless ingredients mixed together: The quantum miner can theoretically enable an attack on the Bitcoin network: Re-writing parts of the blockchain, reversing transactions, leading to the possibility of a double-spend.56 And indeed, a quantum miner could use Grover search to perform the Bitcoin proof-of-work using quadratically fewer hashes than are needed classically.57 If all of these combined unlikelihoods come true and the quantum miner could maintain the 51% attack long enough, the Bitcoin network would indeed have an existential crisis. The chances of this event ever occurring are theoretically possible (that’s a nice way of saying it never will).
And even if it were to happen; proof-of-work models without a quantum advantage exist – meaning that the proof-of-work can’t be accomplished significantly faster with a quantum computer than with a classical computer (e.g., memory-intensive proof-of-works such as Momentum,58 Cuckoo Cycle,59 and Equihash60). But changing to a new mining algorithm is not as easy as it might sound, especially in an emergency setting: The forked chain would immediately lose the entire hash rate because the current ASIC miners do not support the new algorithm. Meaning that the safety of the network would be severely compromised.
Conclusion:
The threat of quantum computers for Bitcoin is not as intimidating as it is often portrayed. Bitcoin has multiple quantum vulnerabilities, the realistic one to theoretically be exploited one day being unveiled public keys. It is not unlikely that hundreds of thousands of lost Bitcoins will be obtained by quantum computers one day.
For all other described quantum vulnerabilities, the combination of
- the network’s capacity to evolve (to resist attacks) and
- the quantum-proof solutions available (which are just seen as an overkill so far)
provide Bitcoin with the tools needed to mitigate such threats, even in the case of very high-capacity quantum computers.
Many experts discuss the potential adverse effects quantum computing has for Bitcoin (which are true) but dismiss its capacity to adapt and improve. Vulnerabilities exist, but so do solutions. The exposure of the vulnerabilities mentioned above is still several years away, and countermeasures can be implemented safely. The quantum threat is not entirely far-fetched but definitely exaggerated. Quantum computers will eventually break the current Bitcoin system, but Bitcoin will already have evolved until that has happened.
You can get more information about the author -Michael Weymans – here on LinkedIn.
Original source: https://blog.bitbeginner.com/p/quantum-computers